Basic Router Lab
1. Building your first network
As your first network lab you are going to | Look on performing basic configurations in network nodes and configuring a network. In detail you will be configure the switch management interface and implement basic connectivity between two user terminals. You are going to learn about basic but useful diagnostic commands for networking.
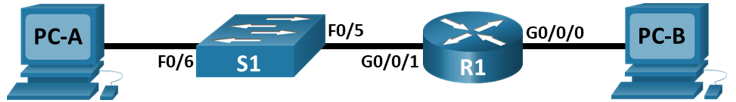
Figure 1 Basic topo| Logy
Table 1 Addressing table.
| Device | Interface | IP Address / Prefix | Default Gateway |
|---|---|---|---|
| R1 | G0/0/0 | 192.168.0.1 /24 | N/A |
| 2001:db8:acad::1 /64 | |||
| fe80::1 | |||
| G0/0/1 | 192.168.1.1 /24 | ||
| 2001:db8:acad:1::1 /64 | |||
| fe80::1 | |||
| Loopback0 | 10.0.0.1 /24 | ||
| 2001:db8:acad:2::1 /64 | |||
| fe80::1 | |||
| PC-A | NIC | 192.168.1.10 /24 | 192.168.1.1 |
| 2001:db8:acad:1::10 /64 | fe80::1 | ||
| PC-B | NIC | 192.168.0.10 /24 | 192.168.0.1 |
| 2001:db8:acad::10 /64 | fe80::1 |
-
If you are unable to construct the network you can download the solution file here:
Scenario
This is a comprehensive lab to review previously covered IOS router commands. In Parts 1 and 2, you will cable the equipment and complete basic configurations and interface settings on the router.
In Part 3, you will use SSH to connect to the router remotely and utilize the IOS commands to retrieve information from the device to answer questions about the router.
Part 1: Set Up the Topology and Initialise Devices
-
Cable the network as shown in the topology.
- Attach the devices as shown in the topology diagram, and cable as necessary.
- Power on all the devices in the topology.
-
Initialize and reload the router and switch.
Part 2: Configure Devices and Verify Connectivity
-
Configure the PC interfaces.
-
Configure the IP address, subnet mask, and default gateway settings on PC-A.
-
Configure the IP address, subnet mask, and default gateway settings on PC-B.
-
-
Configure the router
-
Console into the router and enable privileged
EXECmode. -
Enter configuration mode.
-
Assign a device name to the router.
-
Set the router’s domain name as
ccna-lab.com. -
Disable DNS lookup to prevent the router from attempting to translate incorrectly entered commands as though they were host names.
-
Encrypt the plaintext passwords.
-
Configure the system to require a minimum 12-character password.
-
Configure the username
SSHadminwith an encrypted password of55Hadm!n2020. -
Generate a set of crypto keys with a 1024 bit modulus
-
Assign the privileged
EXECpassword to$cisco!PRIV* -
Assign
$cisco!!CON*as the console password, configure sessions to disconnect after four minutes of inactivity, and enable login. -
Assign
$cisco!!VTY*as thevtypassword, configure thevtylines to accept SSH connections only, configure sessions to disconnect after four minutes of inactivity, and enable login using the local database. -
Create a banner that warns anyone accessing the device that unauthorized access is prohibited.
-
Enable IPv6 Routing
-
Configure all three interfaces on the router with the IPv4 and IPv6 addressing information from the addressing table above. Configure all three interfaces with descriptions. Activate all three interfaces.
R1(config)# interface g0/0/0 R1(config-if)# ip address 192.168.0.1 255.255.255.0 R1(config-if)# ipv6 address fe80::1 link-local R1(config-if)# ipv6 address 2001:db8:acad::1/64 R1(config-if)# description Connection to PC-B R1(config-if)# no shutdown R1(config-if)# exit R1(config)# interface g0/0/1 R1(config-if)# ip address 192.168.1.1 255.255.255.0 R1(config-if)# ipv6 address fe80::1 link-local R1(config-if)# ipv6 address 2001:db8:acad:1::1/64 R1(config-if)# description Connection to S1 R1(config-if)# no shutdown R1(config-if)# exit R1(config)# interface loopback0 R1(config-if)# ip address 10.0.0.1 255.255.255.0 R1(config-if)# ipv6 address fe80::1 link-local R1(config-if)# ipv6 address 2001:db8:acad:2::1/64 R1(config-if)# description loopback adapter R1(config-if)# no shutdown R1(config-if)# exit -
The router should not allow vty logins for two minutes if three failed login attempts occur within 60 seconds.
-
Set the clock on the router.
-
Save the running configuration to the startup configuration file.
-
-
What would be the result of reloading the router prior to completing the
copy running-config startup-configcommand?- The contents of the running configuration in RAM would be erased during reload. As a result, the router would boot up without a startup configuration and the user would be asked if they would like to enter initial configuration dialog.
-
Verify network connectivity.
- Using the command line at PC-A, ping the IPv4 and IPv6 addresses for PC-B.
-
Remotely access R1 from PC-A using the Tera Term SSH client.
- Using Tera Term on PC-A, open an
SSHsession to theR1Loopback interface IPv4 address. Ensure that the SSH radio button is selected and then click OK to connect to the router. Log in asSSHadminwith the password55Hadm!n2020.
- Using Tera Term on PC-A, open an
-
Using Tera Term on PC-A, open an SSH session to the R1 Loopback interface IPv6 address.
- Ensure that the SSH radio button is selected and then click OK to connect to the router.
- Log in as
SSHadminwith the password55Hadm!n2020.
Part 3: Display Router Information
In Part 3, you will use show commands from an SSH session to retrieve information from the router.
Establish an SSH session to R1.
- Using Tera Term on PC-B, open an SSH session to the R1 Loopback interface IPv6 address and log in as
SSHadminwith the password55Hadm!n2020.
Retrieve important hardware and software information.
-
Use the show version command to answer questions about the route
-
The
showcommands often provide multiple screens of outputs. Filtering the output allows a user to display certain sections of the output. To enable the filtering command, enter a pipe (|) character after ashowcommand, followed by a filtering parameter and a filtering expression. You can match the output to the filtering statement by using theincludekeyword to display all lines from the output that contain the filtering expression. Filter theshow versioncommand, usingshow version | include registerto answer the following question:What is the boot process for the router on the next reload?
-
Answers may vary. In most cases (
0x2102), the router will undergo a normal boot, load the IOS from the Flash memory, and load the startup configuration from theNVRAMif present. If the config register is0x2142, the router will bypass the startup config and begin at theuser-modecommand prompt. If the initial boot fails, the router goes intoROMMONmode.R1# show version | include register Configuration register is 0x2142 (will be 0x2102 at next reload)
-
-
Display the start up configuration using
show startup-config
How are passwords presented in the output?
-
Passwords are encrypted due to the service password-encryption command.
-
Use the
show startup-config | section vtycommand.R1# show startup-config | section vty line vty 0 4 exec-timeout 4 0 password 7 15560805172924656905011B59 login local transport input ssh
-
-
Display the routing table on the router using the
show ip routecommand on the router to answer the following questions:
-
Display a summary list of the interfaces on the router using the
show ip interface briefcommand on the router to answer the following question: -
Use the
show ipv6 int briefcommand to verify IPv6 settings on R1.
- On PC-B, change its configuration so that it no longer has a static IPv6 address. You may have to reboot the machine. Then, issue the
ipconfigcommand on PC-B to examine the IPv6 configuration.
Part 4: Reflection Questions
-
In researching a network connectivity issue, a technician suspects that an interface was not enabled.
-
In researching a network connectivity issue, a technician suspects that an interface was assigned an incorrect subnet mask.